Implementing Aruba Campus Access v23.112 (IACA)
Welcome to this week's class (IACA)
navigate to https://rubbernecks-arubanetworks.blogspot.com
Day 1 - Lecture Modules & Labs
M00: Course Introduction
Tips on how to google our site for documentation
- googling for AOS-Switch-related topics
- site:hpe.com 16.09 -inurl:pdf -inurl:cx "dhcp-snooping"
- googling for AOS-CX-related topics
- site:arubanetworks.com -inurl:pdf inurl:AOS-CX inurl:10\.11 "dhcp-snooping"
- search option notes:
- site:x only searched that domain
- -inurl:x don't report links with this text in the URL
- inurl:x only report on links with text
- (ideal for finding specific version documentation)
Helpful Links
- about Aruba training and this course
- where to find more information
- vsg: ESP Campus Deploy
- aruba: Aruba Technical Product Documentation Portal
- here you find:
- Technology Briefs
- Validated Reference Designs
- Aruba Validated Designs
- Compliancy Documentation related to GDPR
- airheads: community.arubanetworks.com
- abc: Airheads Broadcasting Channel
- afp: Partner Technical Webinars
- aruba: Central Demo
- where to find online documentation
- asp: Aruba Documentation Portal (all products)
- techdocs: The CLI Bank (all products)
- asp: Central Latest Online Help
- asp: Central TroubleShooting Guide (2.5.7)
- techdocs: The CLI Bank (all products)
- aps: Central OnPrem_2.5.4 User Guide
- asp: ClearPass Device Insight Online Help
- techdocs: ArubaOS_8.12_Web_Help
- where to find more information
- vsg: ESP Campus Deploy
- aruba: Aruba Technical Product Documentation Portal
- here you find:
- Technology Briefs
- Validated Reference Designs
- Aruba Validated Designs
- Compliancy Documentation related to GDPR
- airheads: community.arubanetworks.com
- abc: Airheads Broadcasting Channel
- afp: Partner Technical Webinars
- aruba: Central Demo
- where to find online documentation
- asp: Aruba Documentation Portal (all products)
- techdocs: The CLI Bank (all products)
- asp: Central Latest Online Help
- asp: Central TroubleShooting Guide (2.5.7)
- techdocs: The CLI Bank (all products)
- aps: Central OnPrem_2.5.4 User Guide
- asp: ClearPass Device Insight Online Help
- techdocs: ArubaOS_8.12_Web_Help
- ClearPass Policy Manager specific links
- ClearPass Policy Manager specific links
- AOS-CX specific links
- AOS-CX specific links
- aruba: feature-navigator.arubanetworks.com
- asp: CX Documentation Portal
- asp: CX_10.13 IP Services Guide
- asp: CX_10.13 Security Guide
- asp: CX_10.13 NAE
- asp: CX_10.13 Monitoring Guide
- asp: CX_10.12 ACLs and Classifier Policies Guide - 6[34]00,81xx,8360
- asp: CX_10.13 CoPP Guide
- asp: CX_10.13 Layer-2 Bridging Guide
- asp: CX_10.12 IP Routing
- asp: CX_10.13 Fundamentals Guide
- www.arubanetworks.com/assets/ds/DS_4100iSwitchSeries.pdf
- www.arubanetworks.com/assets/ds/DS_6000Series.pdf
- www.arubanetworks.com/assets/ds/DS_6100Series.pdf
- www.arubanetworks.com/assets/ds/DS_6200Series.pdf
- www.arubanetworks.com/assets/ds/DS_6300Series.pdf
- www.arubanetworks.com/assets/ds/DS_6400Series.pdf
- www.arubanetworks.com/assets/ds/DS_8100Series.pdf
- www.arubanetworks.com/assets/ds/DS_8320Series.pdf
- www.arubanetworks.com/assets/ds/DS_8325Series.pdf
- www.arubanetworks.com/assets/ds/DS_8360Series.pdf
- www.arubanetworks.com/assets/ds/DS_8400Series.pdf
- www.arubanetworks.com/assets/ds/DS_9300Series.pdf
- www.arubanetworks.com/assets/ds/DS_10000Series.pdf
- aruba: feature-navigator.arubanetworks.com
- asp: CX Documentation Portal
- asp: CX_10.13 IP Services Guide
- asp: CX_10.13 Security Guide
- asp: CX_10.13 NAE
- asp: CX_10.13 Monitoring Guide
- asp: CX_10.12 ACLs and Classifier Policies Guide - 6[34]00,81xx,8360
- asp: CX_10.13 CoPP Guide
- asp: CX_10.13 Layer-2 Bridging Guide
- asp: CX_10.12 IP Routing
- asp: CX_10.13 Fundamentals Guide
- www.arubanetworks.com/assets/ds/DS_4100iSwitchSeries.pdf
- www.arubanetworks.com/assets/ds/DS_6000Series.pdf
- www.arubanetworks.com/assets/ds/DS_6100Series.pdf
- www.arubanetworks.com/assets/ds/DS_6200Series.pdf
- www.arubanetworks.com/assets/ds/DS_6300Series.pdf
- www.arubanetworks.com/assets/ds/DS_6400Series.pdf
- www.arubanetworks.com/assets/ds/DS_8100Series.pdf
- www.arubanetworks.com/assets/ds/DS_8320Series.pdf
- www.arubanetworks.com/assets/ds/DS_8325Series.pdf
- www.arubanetworks.com/assets/ds/DS_8360Series.pdf
- www.arubanetworks.com/assets/ds/DS_8400Series.pdf
- www.arubanetworks.com/assets/ds/DS_9300Series.pdf
- www.arubanetworks.com/assets/ds/DS_10000Series.pdf
- AP Datasheets
- AP Datasheets
- Remote APs
- Indoor APs
- www.arubanetworks.com/assets/ds/DS_AP303Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP503Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP500Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP510Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP530Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP550Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP610Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP630Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP650Series.pdf
- Outdoor/Ruggedized APs
- www.arubanetworks.com/assets/ds/DS_AP360Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP370Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP518Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP560Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP570Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP580Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP670Series.pdf
- GW Datasheets
- Remote APs
- Indoor APs
- www.arubanetworks.com/assets/ds/DS_AP303Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP503Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP500Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP510Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP530Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP550Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP610Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP630Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP650Series.pdf
- Outdoor/Ruggedized APs
- www.arubanetworks.com/assets/ds/DS_AP360Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP370Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP518Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP560Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP570Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP580Series.pdf
- www.arubanetworks.com/assets/ds/DS_AP670Series.pdf
- GW Datasheets
M01: Intro to Aruba Solutions
Lunch Break
M02: Building Wired Infrastructure
Lab 1 - Testing Remote Lab Connectivity
- 1.1: Aruba Training Remote Lab Access
- page 7
- when you login to arubatraininglab.computerdata.com be sure that the login page is fully loaded before you press submit
- page 16:
- be sure to click "SSO" before you try to login to Central
- 1.2: Testing Connectivity
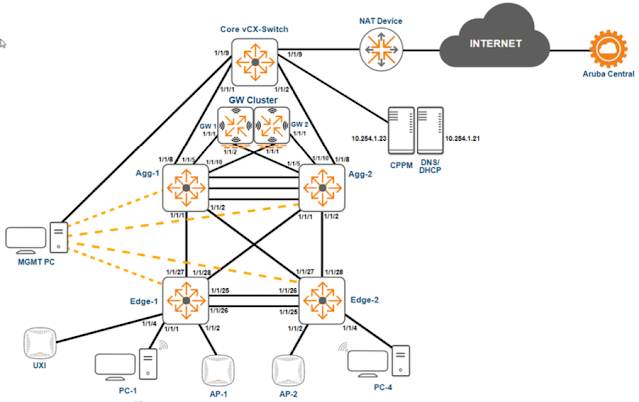
Lab 2.1 - Campus Wired Aggregation - VSX
- 2.1.1: Review the Initial Configuration
- 2.1.2: VSX Basic Configuration
- 2.1.3: Configure a VSX LAG
- 2.1.4: Configure VSX L3 SVI with Active Gateway
- if your edge-1 or edge-2 switches cannot establish control-plane with central after they inherit configuration from the group, check if it has dns setup, if not... add this to your template
- ip dns server-address 10.254.1.21
- use the following command to debug
- debug central all
- debug destination buffer
- clear debug all
- show debug destination
- 2.1.5: VSX Link-Up delay
- 2.1.6: VSX Split-brain detection
Lab 2.2 - Wired Routing
- 2.2.1: Basic OSPF Configuration
- 2.2.2: Route Redistribution and Filtering Using Route Maps
- 2.2.3: Multi-Area OSPF and Route Aggregation between Area
- 2.2.4: Enhance OSPF Neighbor State Detection with BFD
Lab 2.3 - Campus Wired with Central
- 2.3.1: Onboard a switch to Central with ZTP
- 2.3.2: Aruba Central Initial Access
- 2.3.3: Managing Edge Switches using a Template Group
- 2.3.4: Migrate Aggregation Switches to Aruba Central
Helpful commands
- show lacp interfaces
- show lldp neighbor-info
- show spanning-tree
- show event -r -n5
- show running-config vsx vsx-peer
- show running-config vsx-sync peer-diff
- show vsx status
- show vsx status linkup-delay
- show vsx status keepalive
- policy mirror reset
- show ip ospf neighbors
- show ip ospf interface brief
- show ip ospf lsdb
- show ip ospf lsdb external
- show ip ospf lsdb area 0
- show ip ospf lsdb database-summary
- show ip route
- show ip dhcp
- show lacp interfaces
- show aruba-central
Day 2 - Lecture Modules & Labs
M03: Wireless Infrastructure with Aruba Gateways
Lab 3.1 - Deploying APs
- 3.1.1: Deploying APs
Lab 3.2 - Deploying APs
- 3.2.1: Configure Gateway1 using the Setup Dialog
- 3.2.2: Configuring the Gateway in Aruba Central
- 3.2.3: Monitor Gateway Configuration Changes from Central
Lab 3.3 - Automatic Gateway Clustering
- 3.3.1: Review the Existing Auto Cluster
Helpful commands
- branchspport / mac-address (if not connected to central)
- show configuration setup-dialog
- show port status
- show interface port-channel 0
- show lacp 0 neighbor
- show log all 6 | include fpapps
- show lc-cluster group-profile
- show lc-cluster group-profile auto_gwcluster_xyz_0
- show lc-cluster group-membership
M04: Tunneled WLAN Architecture
Lab 4.1 - Deploy Tunnel WLAN
- 4.1.1: Review the Wired Network
- 4.1.2: Create PSK Tunnel WLAN with the GW Cluster
- 4.1.3: Review the Configuration
- 4.1.4: Verify the Operation of the Tunnel WLAN
- 4.1.5: Configure GRE over IPsec
Lab 4.2 - Tunneled WLAN Cluster Operation
- 4.2.1: Review the Cluster Status
- 4.2.2: Cluster Bucket Map
- 4.2.3: Load Distribution and Failover
Lunch Break
M05: Secure Enterprise WLAN
More About Radius Access-Accept Attributes
- slide 15: service-type=framed
- requires auth parameters to then establish/allow access to the network
- slide 11: service-type=call-check
- used to verify the status of a call
- does not support session timeouts
- it is more about monitoring call status rather than establishing access
Lab 5.1 - Deploy Tunnel Corporate WLAN
- 5.1.1: Understanding the AAA Profile on PSK WLAN
- 5.1.2: Configure Corporate 802.1X Tunnel WLAN
- 5.1.3: Connect with a WLAN Client
- 5.1.4: Monitoring and Roaming Key Distribution
Lab 5.2 - Roles and Access Control
- 5.2.1: User Role Derivation
- 5.2.2: Use the WLAN Workflow to Apply Access Control
- 5.2.3: Gateway Controlled Access Control
- 5.2.4: Gateway Controlled Access Control using the User Alias
- 5.2.5: Configure Dynamic Authorization with the Gateway Cluster
- 5.2.6: (optional) Server Rule-based Role Derivation
Day 3 - Lecture Modules & Labs
M06: Guest and Captive Portal
Lab 6 - Overlay Guest WLAN with ClearPass Guest
- 6.1: Verify a ClearPass Guest page
- 6.2: Configure WLAN Profile with ClearPass Guest Splash Page
- 6.3: Test ClearPass Guest access
- 6.4: Guest Authentication with ClearPass MAC Caching
- 6.5: (optional) Web Redirect for a Corporate User
M07: Wireless Authentication for IOT
Lab 7 - PSK IOT WLAN
- 7.1: Create MPSK Local Overlay WLAN
- 7.2: Configure ClearPass-based Role Mapping for MPSK
Lunch Break
M08: Mixed Mode Architecture
Lab 8 - Configuring Mixed Forwarding WLAN
- 8.1: Employee WLAN with Mixed Mode
- 8.2: RADIUS-based VLAN Assignment
- 8.3: (optional) Custom RADIUS Attribute in a VLAN Rule
M09: Gateway Cluster Deployments
Lab 9 - Gateway Cluster Deployments
- 9.1: Move Gateway GW2 to the Group Campus-Main-DMZ
- 9.2: Multi-Zone
- 9.3: Set up Site-Based Clustering Using a Single Site
- 9.4: Site-Based Clustering using Multiple Sites
- 9.5: (optional) Site-Based Cluster with Group-Based Backup Cluster
Day 4 - Lecture Modules & Labs
M10: Wired Port Access
- techdocs: AOS-CX 10.10 Security Guide > Port access > Mixed roles
- how VSA attributes can override LUR or DUR attributes
- abc: AOS-CX 10.10 - Support for MACsec with EAP TLS Update
- abc: Aruba ClearPass Workshop - Wired #4 - Dynamic Access List (dACL)
- shows how to implement IETF NAS-FILTER-RULES
- techdocs: AOS-CX 10.10 Security Guide > Port access > Mixed roles
- how VSA attributes can override LUR or DUR attributes
- abc: AOS-CX 10.10 - Support for MACsec with EAP TLS Update
- abc: Aruba ClearPass Workshop - Wired #4 - Dynamic Access List (dACL)
- shows how to implement IETF NAS-FILTER-RULES
Lab 10.1 - Wired Access Control
- 10.1.1: Configure sw-edge2 for Access Control and 802.1X
- 10.1.2: Enable MAC Authentication
- 10.1.3: User Roles with Device-Based Authentication
Lab 10.2 - Wired Access with Aruba Gateways
- 10.2.1: Prepare the Gateway
- 10.2.2: Configure the Switch-to-Gateway Cluster Connection
- 10.2.3: (optional) Troubleshooting and Failover for UBT
M11: VXLAN and GBP
Lab 11 - Group-Based Policies with EVPN
- 11.1: Prepare your lab environment
- 11.2: Verify the Group-Based Policy Configuration
- 11.3: Configure Access Control Between Roles
Day 5 - Lecture Modules & Labs
M12: Security and Availability Features
Lab 12.1 - Service Survivability
- 12.1.1: Tunnel WLAN Central Survivability
- 12.1.2: Wired Cached Re-Authentication and Critical Role
Lab 12.2 - Admin Authentication
- 12.2.1: Gateway Admin Authentication
- 12.2.2: Switch Admin Authentication
M13: Traffic Optimization and QOS
- asp: UCC - What is the difference between Upstream and Downstream UCC Scores
- abc: ArubaOS 8.9 Series – Part 11 – QoS & AirSlice
- skip ahead to 9m23s to get to AirSlice
- asp: UCC - What is the difference between Upstream and Downstream UCC Scores
- abc: ArubaOS 8.9 Series – Part 11 – QoS & AirSlice
- skip ahead to 9m23s to get to AirSlice
Lab 13 - Traffic Optimization
- 13.1: WLAN Optimization
- 13.2: Wired QoS
- 13.3: Wireless QoS Marking
- 13.4: Wireless WMM Voice Class
- 13.5: (optional) AirMatch Configuration
M14: Monitoring
Lab 14 - Monitoring with UXI Sensors
- 14.1: Monitoring with the Aruba UXI Sensor
- 14.2: Integrate the UXI Dashboard with Aruba Central
- 14.3: Reset the Lab Customer Environment
Appendix
Acronyms or Key terms
- ESP: Encapsulating Security Payload
- SA: Security Association
- a relationship between two or more entities that describes how the entities will use security services to communicate securely
- SPI: Security Parameter Index
- identification tag added to the header while using IPsec for tunneling the IP traffic.
- This tag helps the kernel discern between two traffic streams where different encryption rules and algorithms may be in use
- nonce:
- random / semi-random number generated for cryptographic communication
- mechanism helps to protect against replay attacks
- the term stands for "number used once"
Lab Access Errata


Comments
Post a Comment